Microsoft Sentinel has evolved far beyond a traditional cloud-native SIEM. In 2026, it is shaping into a unified SecOps data and analytics platform, deeply integrated with Microsoft Defender, powered by a new Sentinel Data Lake, enhanced ingestion controls, and platform-level correlation.
This article focuses purely on the technical engineering side of Sentinel — architecture, ingestion design, analytics behavior, data lake strategy, automation, and cost control.
📌 Why this matters
If you are:
- Designing a new Sentinel deployment
- Migrating from another SIEM
- Optimizing an existing workspace
Then success in 2026 depends less on “connecting logs” and more on:
- Data lake architecture
- DCR-based ingestion filtering
- Normalization (ASIM)
- Defender correlation behavior
- Cost engineering
📑 Table of contents
- Sentinel architecture in 2026
- Sentinel Data Lake — design & retention
- Ingestion architecture & Data Collection Rules
- Normalization & ASIM
- Analytics rules, Fusion & Defender correlation
- Automation & SOAR engineering
- Cost engineering strategies
- Advanced KQL examples
- Implementation checklist
- Microsoft reference links
1️⃣ Sentinel Architecture in 2026
The most fundamental change is Sentinel’s evolution into a Defender-native SIEM layer with split analytics and data lake storage.
🔧 High-level architecture diagram
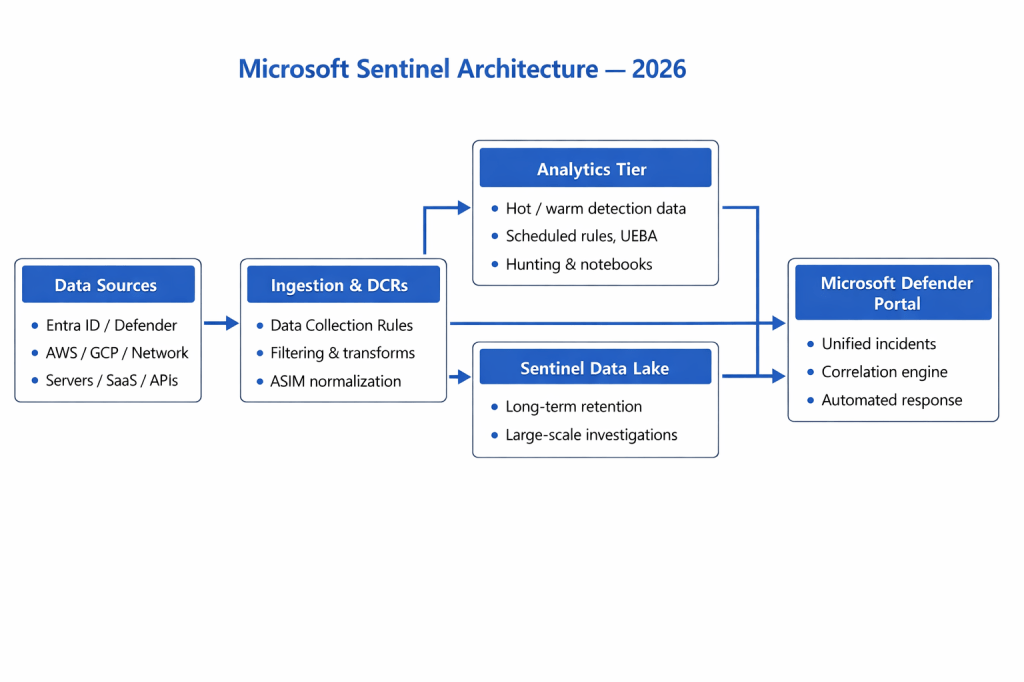
Architectural flow
Telemetry → DCR filtering → Analytics tier (hot) + Data lake (cold) → Defender correlation → Unified incidents & SOARThis is no longer a pure SIEM pipeline — it is now a security data platform.
2️⃣ Sentinel Data Lake — design & retention strategy
Microsoft introduced a separate Sentinel Data Lake tier to decouple storage from analytics.
Why this is critical
- Long retention without SIEM query cost explosion
- Large-scale historical hunting
- Compliance and forensic readiness
- Defender telemetry can land directly in the lake
Engineering model
| Tier | Purpose |
|---|---|
| Analytics tier | Detections, near-real-time correlation |
| Data Lake tier | Long-term, cold, large-volume security data |
Example retention strategy
- SigninLogs: 180 days analytics → 2 years lake
- EDR telemetry: 90 days analytics → 2 years lake
- DNS / proxy: 30 days analytics → lake-only
- Compliance logs: lake-only
Microsoft docs
- Sentinel Data Lake overview:
https://learn.microsoft.com/en-us/azure/sentinel/datalake/sentinel-lake-overview - Manage data tiers & retention:
https://learn.microsoft.com/en-us/azure/sentinel/manage-data-overview - Set up Data Lake: https://jeffreyappel.nl/microsoft-sentinel-data-lake-how-to-use-enable-and-set-up-the-unified-datalake/
3️⃣ Ingestion architecture & Data Collection Rules (DCRs)
In 2026, DCRs are not optional. They are the foundation of cost control and data quality.
What DCRs enable
- Event-level filtering
- Field-level transformations
- ASIM alignment
- Routing to analytics vs lake tier
Engineering principle
❌ Send everything → filter later → pay more
✅ Filter early → normalize → store what matters
Microsoft docs
- DCR overview:
https://learn.microsoft.com/en-us/azure/azure-monitor/data-collection/data-collection-rule-overview
4️⃣ Normalization & ASIM (non-negotiable)
Microsoft’s detection and UEBA engines increasingly rely on ASIM-normalized schemas.
Why this matters
- Cross-source detections work
- UEBA baselines stabilize
- Fusion correlation improves
- Hunting queries become reusable
Microsoft docs
- ASIM normalization:
https://learn.microsoft.com/en-us/azure/sentinel/normalization - Data connectors reference:
https://learn.microsoft.com/en-us/azure/sentinel/data-connectors-reference
5️⃣ Analytics rules, Fusion & Defender correlation
Sentinel analytics no longer work in isolation.
Microsoft is consolidating SIEM and XDR correlation inside the Defender portal.
Technical impact
- XDR alerts and SIEM detections merge
- Fusion logic operates at platform level
- Incident shapes and grouping may change
Migration guidance
https://learn.microsoft.com/en-us/azure/sentinel/move-to-defender
Engineering recommendation
After migration, always re-validate:
- Incident grouping
- Automation triggers
- Alert suppression
- Severity logic
6️⃣ Automation & SOAR engineering
Sentinel SOAR in 2026 should follow decision-first automation.
High-value automation use cases
- Threat intelligence enrichment
- Identity risk scoring
- Auto-closure of known false positives
- Conditional containment
Design principle
Automate context before containment.
Never auto-block without validation logic.
7️⃣ Cost engineering (most teams fail here)
Sentinel cost is architecture-driven.
Major cost drivers
- Ingested GB/day
- Retention duration
- Analytics tier volume
- Query frequency
Cost visibility KQL
Usage | where TimeGenerated > ago(32d)| where StartTime >= startofday(ago(31d)) and EndTime < startofday(now())| where IsBillable == true| summarize BillableDataGB = sum(Quantity) / 1000 by Solution, DataType| sort by Solution asc, DataType ascMicrosoft pricing
https://www.microsoft.com/en-in/security/pricing/microsoft-sentinel
8️⃣ Advanced KQL examples
Ingestion-aware failed logon detection
let ingestion_delay = 5m;SigninLogs| where TimeGenerated > ago(1h + ingestion_delay)| where ResultType != "0"| summarize Failed = count() by UserPrincipalName, bin(TimeGenerated, 5m)| where Failed > 10Identify noisy data sources
Heartbeat| summarize Events = count() by Computer, bin(TimeGenerated, 1d)| top 10 by EventsCost trend visibility
Usage| where Entity == "Ingestion"| summarize GB = sum(Quantity) by bin(TimeGenerated, 1d)9️⃣ Implementation checklist
- Inventory connectors and parsers
- Design analytics vs lake retention
- Deploy DCRs as code
- Enforce ASIM mapping
- Validate Defender correlation behavior
- Optimize expensive KQL rules
- Implement automation rules
- Review ingestion cost weekly
🔗 Microsoft reference links
- What’s new in Sentinel (Jan 2026)
https://techcommunity.microsoft.com/blog/microsoftsentinelblog/what%E2%80%99s-new-in-microsoft-sentinel-january-2026/4486109 - Sentinel Data Lake
https://learn.microsoft.com/en-us/azure/sentinel/datalake/sentinel-lake-overview - Manage data tiers
https://learn.microsoft.com/en-us/azure/sentinel/manage-data-overview - Move to Defender portal
https://learn.microsoft.com/en-us/azure/sentinel/move-to-defender - DCR overview
https://learn.microsoft.com/en-us/azure/azure-monitor/data-collection/data-collection-rule-overview - ASIM normalization
https://learn.microsoft.com/en-us/azure/sentinel/normalization - Sentinel pricing
https://www.microsoft.com/en-in/security/pricing/microsoft-sentinel
🎯 Final note
Microsoft Sentinel in 2026 is not “log management.”
It is:
- A security data platform
- A correlation engine
- A SOAR orchestrator
- A cost-engineering challenge
Real Sentinel expertise now lies in architecture, data modeling, and detection engineering.

Leave a comment